
Two days ago, Joyce and I separately received an email from one of our customers. It didn’t look important to me so I didn’t do anything with it when it arrived. Joyce, however, looked at the email and something told her it wasn’t on the up and up. Yes, it was from our customer’s legitimate email address (not one that’s made to look real but is from a foreign country) and, yes, it had her correct name. But, it had an attachment and for some reason she just didn’t trust it. What did she do? She forwarded it to me and asked me to check it out. Now, I had to pay attention to it!

The attachment looked innocent enough – OneDrive.pdf. Customer’s often ask us about OneDrive when they have no clue what it is. The idea of sending us an email about it is not unusual. However, it’s rare that a customer sends us attachments, so it made sense for Joyce to be leery.
As it turns out, our customer’s email account had been hacked. He didn’t know that until we called him. Once the hacker was in the account, he or she sent out emails with the OneDrive.pdf attachment. The attachment is a phishing attempt. (Not sure what phishing is? Read our blog post from January 29, 2019 called “Let’s Go Phishing!”)
When you clicked on the attachment, this is what you would see:

The page looks like a legitimate Microsoft OneDrive page and it showed that my customer had a document for me to view (I’ve blocked out his name to protect the innocent! LOL) If I clicked on “View Document,” another page would open. By the time I investigated this attachment, Microsoft had already identified the next web page as a phishing attempt and I received this window:
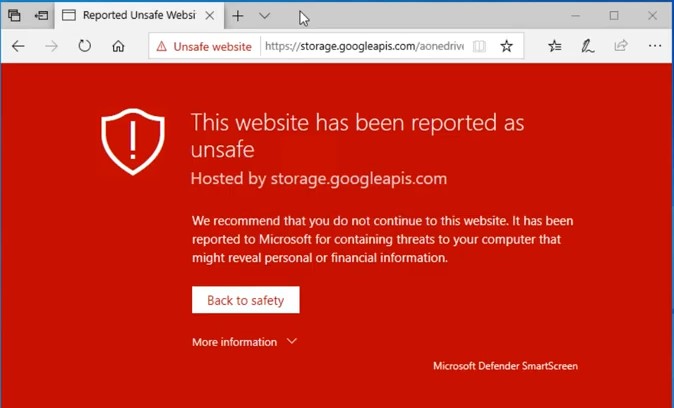
Because of this warning, I was protected from the phishing attempt. However, if I had clicked on the attachment before Microsoft became aware of the evil doing, I would have seen this screen:

The hacker/scammer gave me the opportunity to use my email to log in and see the document. I could choose from a variety of well-known email domains (Google, Yahoo, AOL, etc.) or I could log in with a domain not listed (the bottom option). Had I done that, he or she would have captured my user name and password for the account I chose. NOT a good thing! Once the hacker had that information, there are tons of things that could happen. The hacker might steal my contacts or delete all my emails or spam out emails to those in my address book. Also, because the hacker was in my email, he or she might have found out where I bank, where I shop online – other places where I might have used the same user name and password which would give the hacker access. (Security tip: never use the same password you use for your email on any other site.)
Now that you understand what the hacker did, let’s talk about my customer. We had him log in to us and helped him change his password. We also looked to see if the hacker had changed or created any email settings. He/she had! The hacker created 16 rules so that if there were any emails kicked back for any reason, they would go straight to the Trash box. If our customer never looked in Trash, he’d never know anything was sent out until someone called him, like we did. Obviously, we deleted all those rules. When we looked in Trash, there were, indeed, emails with the OneDrive.pdf attachment which were returned as undeliverable.
The lesson here? Be leery of any emails with attachments unless you were expecting them. This email from our customer looked legit. It was only Joyce’s intuition that brought our attention to this phishing attempt.
Want to know how I safely tested the email attachment without any chance of infecting my computer? I explain it all in this video which I created yesterday:
